[ad_1]
Cryptography is basically necessary as a result of it means that you can securely shield information that you don’t need anybody else to have entry to. It’s used to guard company secrets and techniques, safe categorized info and to guard private info to protect in opposition to issues like identification theft.
In the present day’s submit is principally going to be about cryptography, now earlier than we truly bounce into the principle submit, let me offer you guys a quick on the matters that we will cowl as we speak.
So to begin with, we will cowl what’s cryptography by the assistance of a really simplistic state of affairs.
Then we’re going to undergo the classifications of cryptography and the way the completely different classificative algorithm books
What’s Cryptography
I will take the assistance of an instance or a state of affairs to really clarify what’s cryptography.
So for instance now we have an individual and let’s name him Andy. Now suppose Andy sends a message to his buddy Sam who’s on the opposite aspect of the world.
Clearly he desires this message to be personal and no one else ought to have entry to the message. He makes use of a public discussion board for instance, the web for sending this message. The objective is to really safe this communication.
And naturally now we have to be safe in opposition to somebody. Now, for instance there’s a good man referred to as Eve who has secretly received entry to your communication channel. Since this man has entry to your communication. He can do way more than simply eavesdrop. For instance, he can attempt to change the message in itself. Now, that is only a small instance.
What if Eve truly will get entry to your personal info? Effectively, that would truly end in a giant disaster. So how can Andy ensure that no one within the center may entry the message despatched to Sam the objective right here is to make communication safe and that is the place cryptography is available in.
So what precisely is cryptography? Effectively cryptography is the apply and the research of methods for securing communication and information within the presence of adversaries.
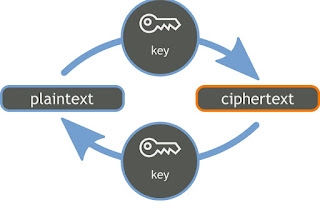
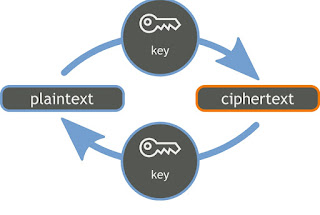
So let me take a second to elucidate how that truly occurs. Effectively, to begin with, now we have a message this message is firstly transformed right into a numeric type after which this numeric type is utilized with a key referred to as an encryption key and this encryption secret is utilized in an encryption algorithm. So as soon as the numeric message and the encryption key has been utilized in an encryption algorithm, what we get is known as a ciphertext.
Now this ciphertext is shipped over the community to the opposite aspect of the world the place the opposite one who the message is meant for, will truly use a decryption key and use the ciphertext as a parameter of a decryption algorithm after which he’ll get what we truly despatched as a message and if some error had truly occurred he’d get an error.
How Cryptography Safe Connection
So let’s examine how cryptography will help safe the connection between Andy and Sam.
So to guard his message Andy first converts his readable message to an unreadable type right here. He converts the message to some random numbers. And after that he makes use of a key to encrypt his message after making use of this key to the numerical type of his message, he will get a brand new worth in cryptography. We name this ciphertext.
So now if Andy sends the ciphertext or encrypted message over communication Channel, he will not have to fret about someone in the course of discovering the personal message.
Even when someone manages to find the message. He will not be capable of decrypt the message with out having a correct key to unlock this message. So suppose Eve right here discovers the message and he one way or the other manages to tamper with the message and message lastly reaches Sam. Sam would wish a key to decrypt the message to get better the unique plain textual content.
Utilizing the important thing he would convert a ciphertext to numerical worth equivalent to the plain textual content. Now after utilizing the important thing for decryption what is going to come out is the unique plain textual content message or an error, now this error is essential. It’s the method Sam is aware of that message despatched by Andy will not be the identical because the message that he acquired.
So the error in a way tells us that Eve has tampered with the message. Now the necessary factor to notice right here is that in fashionable cryptography, the safety of the system purely depends on conserving the encryption and decryption key secret.
Classification of Cryptography
Based mostly on the kind of keys and encryption algorithms cryptography is classed underneath the next classes.
Cryptography is broadly categorized into two classes particularly
- Symmetric key cryptography and
- Uneven key cryptography popularly also referred to as public key cryptography
Symmetric key cryptography is additional categorized as
- Classical cryptography and
- Fashionable cryptography
Additional drilling down classical cryptography is split into two that are
- Transposition cipher and
- Substitution cipher
Alternatively fashionable cryptography is split into
- Stream cipher and
- Block cipher
I am going to broadly clarify all some of these cryptography later. So let’s begin with symmetric key cryptography first.
Symmetric Key Cryptography
Symmetric key algorithms are algorithms for cryptography that use the identical cryptography keys for each encryption of plain textual content and decryption of ciphertext, the keys could also be an identical or there could also be some easy transformation to go between the 2 keys. The keys in apply signify a shared secret between two or extra events that can be utilized to take care of a personal info hyperlink.
This requirement that each events should have entry to the key key is among the major drawbacks of symmetric key encryption compared to publicly encryption also referred to as uneven key encryption.
Symmetric key cryptography is typically additionally referred to as secret key cryptography and the most well-liked symmetric key system is the information encryption requirements, which additionally stands for DES.
Transposition Cipher
Subsequent up, we will talk about transposition cipher. So in cryptography a transposition cipher is a technique of encryption by which the positions held by models of plain textual content, that are generally characters or teams of characters are shifted based on an everyday system in order that the ciphertext constitutes a permutation of the plain textual content that’s the order of models is modified. The plain textual content is reordered.
Now mathematically talking a bijective perform is used on the characters place to encrypt and an inverse perform to decrypt.
So for instance, shall we say, now we have a message which says “meet me after the get together”, now, this has been fastidiously organized within the encryption Matrix, which has been divided into six rows and the columns. So subsequent now we have a key which is principally 4 3 1 6 3 5 after which we rearrange by trying on the plain textual content Matrix after which we get the ciphertext which principally is a few unreadable gibberish at this second. In order that’s how this complete algorithm works.
Alternatively when the ciphertext is being transformed into the plain textual content the plain textual content Matrix goes to be referred and it may be achieved very simply.
Substitution Cipher
Now, we’re going to talk about substitution cipher, substitution of single letters individually easy substitution may be demonstrated by writing out the alphabets in some order to signify the substitution. That is termed a substitution alphabet.
The cipher alphabet could also be shifted or reversed creating the Caesar and upstaged cipher respectively or scrambled in a extra advanced vogue, wherein case it’s referred to as a combined alphabet or deranged alphabet.
Historically combined alphabets could also be created by first writing out key phrase eradicating repeated letters in it. Then writing all of the remaining letters within the alphabet within the traditional order.
Historically the ciphertext is written out in blocks of fastened size omitting punctuations and areas. That is achieved to assist keep away from transmission errors to disguise the phrase boundaries from the plain textual content.
Now, these blocks are referred to as teams and typically a bunch depend that’s the variety of teams is given as a further verify.
Now 5 letter teams are conventional as you guys can see that now we have additionally divided our ciphertext into teams of 5 and this dates again to when messages had been truly was once transmitted by Telegraph.
Now if the size of the message occurs to not be divisible by 5 it could be padded on the finish with nulls and these may be any characters that may be decrypted to apparent nonsense. So the receiver can simply spot them and discard them.
Stream Cipher
Subsequent on our record is stream cipher, a stream cipher is a technique of encrypting textual content to provide ciphertext wherein a cryptographic key and algorithm are utilized to every binary digit in a knowledge stream one bit at a time.
This methodology will not be a lot to make use of in fashionable cryptography. The principle various methodology is block cipher wherein a key and algorithm are utilized to dam of knowledge somewhat than particular person bits in a stream.
Block Cipher
So now that we have spoken about block cipher, let’s go and truly clarify what block cipher does. a block cipher is an encryption methodology that applies a deterministic algorithm to the symmetric key to encrypt a block of textual content somewhat than encrypting one bit at a time as in stream ciphers.
For instance, a typical block cipher AES encrypts 128 bit blocks with a key of predetermined size. That’s both 128, 192 or 256 bits in size.
Now block ciphers are pseudorandom permutation households that function on the fastened dimension of block of bits. These PRPs are perform that can’t be differentiated from utterly random permutation and thus are thought of dependable and been confirmed to be unreliable by some supply.
Uneven Key Cryptography
So now it is time to talk about some uneven cryptography, uneven cryptography also referred to as public key cryptography is any cryptographic system that makes use of pair of keys, which is a public key which can be this emanated extensively and personal keys that are identified solely to the proprietor.
This accomplishes two capabilities authentication the place the general public key verifies {that a} holder of the paired personal keys and the message and encryption the place solely the paired personal key holder can decrypt the message encrypted with the general public key and a public key encryption system. Any particular person can encrypt a message utilizing the receivers public key that encrypted message can solely be decrypted with the receivers personal key.
So to be sensible the era of private and non-private key pair should be computationally economical. The energy of a public key cryptographic system depends on computational efforts required to search out the personal key from its paired public key. So efficient safety solely requires conserving the personal key personal and the general public key may be brazenly distributed with out compromising safety.
How Web site is Secured Utilizing Cryptography
So now that I’ve truly proven you guys how cryptography truly works and the way the completely different classifications are literally utilized. Let’s go and do one thing fascinating. So that you guys are literally studying this submit on this weblog blueguard.ng proper now.
So in the event you guys truly go and click on on the safe half in addition to the URL, you possibly can truly go and examine the digital certificates which might be truly used out right here. So click on on certificates and you will see the main points within the particulars tab.
Now as you guys can see the signature algorithm that’s used for truly securing this web site is being fashionable cipher go well with AES_128_GCM, and it is a very quite common encryption algorithm that’s used all through the web.
Then the signature hash algorithm that’s getting used is AES_128_GCM which makes use of X25519 and the issuer is GTS CA 1D4 and you may get a number of details about websites and all their authority, key identifiers, certificates insurance policies, the important thing utilization and a number of factor about safety simply from this small little button on the market.
In the event you all are nonetheless extra , you all can truly analysis rather a lot on RSA. It is a very in-depth cryptography system. And likewise that brings us to the top of this session.
I hope you guys had enjoyable studying about cryptography and the completely different strategies which might be truly used on the web. That is it for me. Goodbye.
I hope you may have loved studying this submit. Please be type sufficient to share it and you may remark any of your doubts and queries and we’ll reply them on the earliest do look out for extra posts in our content material gallery and comply with Blueguard web site to study extra. Pleased studying.
Bye.
[ad_2]